Create Mass Fake Acces Point On Kali Linux - Today we will play with network using our Kali Linux. I'll write simple ways how to create mass fake AP ( Access Point ) use one of linux hacking tools which installed by default in Kali Linux named mdk3.
Maybe all most of you know if mdk3 is very powerfull network hacking tools, so beware if using this tools. Before take the action, please create your own fake access point list by your favorites text editor. This my own list for example :
Maybe all most of you know if mdk3 is very powerfull network hacking tools, so beware if using this tools. Before take the action, please create your own fake access point list by your favorites text editor. This my own list for example :
- Linux Slaves Labs
- http://linuxslaves.com
- Bala Kurawa
- @wifi.id
- Wifi gratis njing
- Modal Ngob
And please remember saves as .lst extension. I assumed you already have it. Next step activate monitoring mode. Open your terminal, type and run this command below :
airmon-ng start wlan0
Now, this the time for action using network hacking tools mdk3 to create fake AP. Just run this command in your linux terminal :
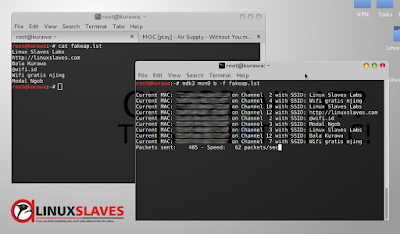
# mdk3 mon0 b -f fakeap.lst
Current MAC: XX:XX:XX:XX:XX:XX on Channel 2 with SSID: Linux Slaves Labs
Current MAC: XX:XX:XX:XX:XX:XX on Channel 4 with SSID: Wifi gratis njing
Current MAC: XX:XX:XX:XX:XX:XX on Channel 10 with SSID: Linux Slaves Labs
Current MAC: XX:XX:XX:XX:XX:XX on Channel 12 with SSID: http://linuxslaves.com
Current MAC: XX:XX:XX:XX:XX:XX on Channel 2 with SSID: @wifi.id
Current MAC: XX:XX:XX:XX:XX:XX on Channel 3 with SSID: Modal Ngob
Current MAC: XX:XX:XX:XX:XX:XX on Channel 3 with SSID: Linux Slaves Labs
Current MAC: XX:XX:XX:XX:XX:XX on Channel 12 with SSID: Bala Kurawa
Current MAC: XX:XX:XX:XX:XX:XX on Channel 7 with SSID: Wifi gratis njing
Current MAC: XX:XX:XX:XX:XX:XX on Channel 9 with SSID: Linux Slaves Labs
Current MAC: XX:XX:XX:XX:XX:XX on Channel 11 with SSID: http://linuxslaves.com
Current MAC: XX:XX:XX:XX:XX:XX on Channel 1 with SSID: @wifi.id
Current MAC: XX:XX:XX:XX:XX:XX on Channel 7 with SSID: Modal Ngob
Current MAC: XX:XX:XX:XX:XX:XX on Channel 3 with SSID: http://linuxslaves.com
Current MAC: XX:XX:XX:XX:XX:XX on Channel 3 with SSID: @wifi.id
Current MAC: XX:XX:XX:XX:XX:XX on Channel 3 with SSID: Wifi gratis njing
Current MAC: XX:XX:XX:XX:XX:XX on Channel 12 with SSID: Linux Slaves Labs
Current MAC: XX:XX:XX:XX:XX:XX on Channel 1 with SSID: Bala Kurawa
Current MAC: XX:XX:XX:XX:XX:XX on Channel 2 with SSID: @wifi.id
Current MAC: XX:XX:XX:XX:XX:XX on Channel 1 with SSID: Modal Ngob
Current MAC: XX:XX:XX:XX:XX:XX on Channel 14 with SSID: http://linuxslaves.com
Current MAC: XX:XX:XX:XX:XX:XX on Channel 5 with SSID: Bala Kurawa
Current MAC: XX:XX:XX:XX:XX:XX on Channel 12 with SSID: Wifi gratis njing
Current MAC: XX:XX:XX:XX:XX:XX on Channel 11 with SSID: Modal Ngob
Current MAC: XX:XX:XX:XX:XX:XX on Channel 11 with SSID: http://linuxslaves.com
Current MAC: XX:XX:XX:XX:XX:XX on Channel 11 with SSID: @wifi.id
Current MAC: XX:XX:XX:XX:XX:XX on Channel 6 with SSID: Modal Ngob
Explanation :
mon0 -> Interface which up by airmon when we activate monitoring modeb -> Beacon Flood Mode which sends beacon frames to show fake APs at clients
-f -> MAC filter bruteforce mode
fakeap.lst - > List of my fake access point that I've created before
You may also read :
- Using Netdiscover to Find IP and Mac Addresses
- Best Operating Systems For Hacking or Penetration Testing 2016
- Steganography Tutorials, Hide Secret Message Within Images
This screenshot will tell you when the attack running in my machine :
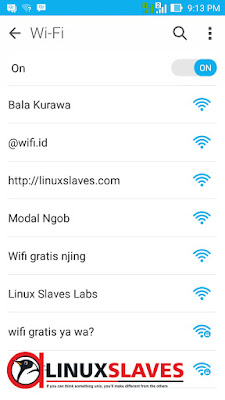
And what will other clients look in their wifi network? Here's screenshot from my ASUS Zenfone 5 :
Explore youself for further activity. I think that's all I can tell about a simple way creating fake acces point on Kali Linux. Thanks for visiting us!